If you’ve been following us a while, you might remember our post all the way back in 2012, where we unveiled our newest, shiny design to bring us into the twenty-teens. The adage about cobblers and shoes we used then once again started ringing true in 2015. We’ve always been in the loop about what makes a great website, even from a design standpoint, but usually those things were reserved to our clients over at The Next Wave and spreading the word to our seminar attendees.
So much has changed even in the three years since our previous design. The biggest of which is the rise of responsive web design, which allows a website to adapt to whatever device a user is viewing the website so that it never looks wrong. With this technology comes a “mobile-first” approach to design, in which websites are designed with mobile devices in mind, then scaled up and enhanced for laptops and desktops.
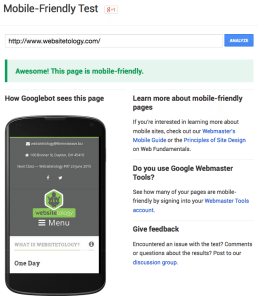
With Google’s mandate that sites be mobile friendly or face consequences in the search engine rankings, we knew we couldn’t wait around any longer to give our site a new facelift. So if you’re reading this post on our website, you’re looking at the new Websitetology design.
Maybe the space aesthetic isn’t your thing. That’s cool. The great thing about the way this site was designed and coded is that the thematic images throughout the site, including the slides on the homepage, can be easily swapped out for new ones without altering a single bit of code. We can return to Earth and give the site a fresh look at a moments notice.
So what do you think? Love it? Have any constructive criticism? Leave your comments below.
Private messaging isn’t really private, at least not unless you encode it. The people at bittorrent know a little more than most do about privacy- and have released a product called “Bleep” which is their entry into true, encrypted private messaging. Of course, both you and your friend have to have the same app installed and figure out a way to find each other.
Bleep functions on a peer-to-peer (or P2P) model, meaning that the messages are being sent directly from one user to the next. Without a middleman, it’s virtually impossible to tell who is talking to whom, and what they are saying. It also offers end-to-end encryption, making sure that your conversation stays truly private.
To get started with Bleep, all that is required is choosing a nickname. You can share your Bleep key (under Settings:Profile) wherever you like: forum post, twitter page, etc. And no one will have any of your other details. Optionally, you can verify your email addresses and mobile numbers with Bleep, which will let your friends discover you through Bleep when they open an account.
In Your Hands, Instead of the Cloud.
Bleep’s logo represents a folded note – a message passed directly, hand-to-hand. In our implementation, we keep messages and the encryption keys for images stored on your local device, not the cloud. For messages and metadata, there is no server for hackers to target and because you hold the keys, images can’t be leaked to haunt you later. We’ve solved serverless peer-to-peer messaging, including the ability to get offline friends your messages when they come back online.
Source: Bleep Now Publicly Available Across All Major Platforms | The Official BitTorrent Blog
The problem with snapchat’s privacy was a simple screen grab could end your privacy- or taking a photo of the device with another device- Bleep brings new levels of security with its “whisper mode”
For parts of a conversation that you’d like to keep temporary, tapping “Go to Whisper” on your phone sends messages and pictures that disappear from devices after they’ve been viewed (25 seconds); holding shift on PC and Ctrl on Mac while hitting send does this on your desktop. You can switch back and forth between normal and whisper messages seamlessly, so you don’t lose the flow of your conversation.
Screenshot, or Not?
Whisper messages have additional protection for screenshots. If a friend manages to capture the screen, they won’t be able to capture who said what, since nicknames are blocked out. And if you forget who you’re whispering with, you tap the “eye” to display the nickname, but the conversation gets blurred. They can capture the conversation or the sender, but not both at the same time.
No matter what- the old maxim holds true- once it’s on the internet- it’s never private.
Read a review here: http://www.macnn.com/articles/15/05/17/new.p2p.instant.messaging.app.helps.keep.conversations.private.128638/
You are being watched online, and it’s not just the NSA. All those products you visited on Amazon that show up in your Facebook feed- those are “remarketing” campaigns- built from tracking your browsing.
Emails you open from a retailer include tracking codes- so when you visit the site, they know who you are- and then customize the site to sell you more.
Or- want to scope out the competition? Why let them know you’ve been looking?
The easiest way to use Tor is to download the Tor Browser. This is a modified version of Firefox along with a bunch of other software that connects you to the Tor network.
Once you’ve downloaded the installer, you have two options: You can just install the software or you can check the installation file’s GPG signature first. Some people like to check the installation file to make sure they’ve downloaded the proper version of the browser and not something that’s been tampered with.
But checking the GPG signature is not a painless process and requires an additional software download. Nevertheless, if that’s something you’d like to do, the Tor Project has a how-to explaining what’s required.
Source: ? How to use the Tor Browser to surf the web anonymously | PCWorld
There are also sites that allow you to do a one off anonymous cloak- like http://www.covertbrowsing.com/ go there, and browse away.
The other end of things is to use a private VPN network that unlinks you from your ISP’s IP. Most of these are services that you pay for- where you “tunnel” all your internet traffic to their servers that become your “home base” IP. Some have cute names, like www.hidemyass.com but, sometimes, that’s not really what they do: read this post: What everybody should know about HideMyAss
People use VPN in order to access content that’s not available on their continent- like Chinese nationals looking for information on democracy- or for American Football fan ex-pats who want to stream NFL games to Europe. Its traditional use is to be a secure way of connecting to their work from remote locations.
But, in the end, remember anything you do online is never private, no matter how careful you are.